Search
TOOLS DON'T MAKE HACKERS, HACKERS MAKE TOOLS. An info sec junkie's professional path. Security Consultant since October 2018. I love hacking and coding and I hope I can give my little knowledge back to the community and help make information systems more secure. This blog focuses on information security and white hat hacking, i.e. hacking based on the client's authorization. Hacking must be done responsibly: don't ruin people's lives and businesses.
Posts
Showing posts from November, 2013
Contact Form
The 5 most common dangers, mistakes and behaviors in IT
- Get link
- X
- Other Apps
Linux Ubuntu 13.10 Saucy Salamander review - the star didn't show up, but the show must go on (part 2)
- Get link
- X
- Other Apps
Linux Ubuntu 13.10 Saucy Salamander review - the star didn't show up, but the show must go on (part 1)
- Get link
- X
- Other Apps
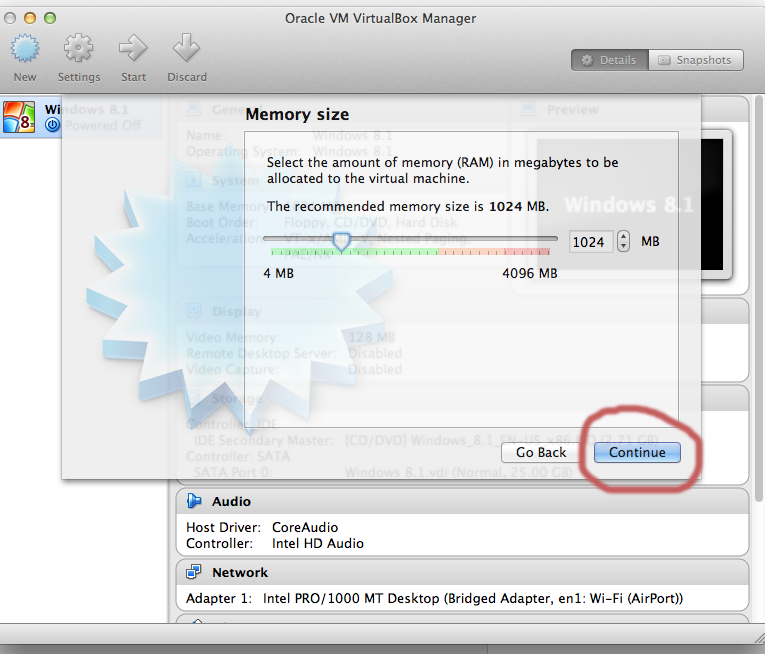
How to emulate Windows 8.1 on a MacOsX Mavericks system with VirtualBox
- Get link
- X
- Other Apps
Windows 8.1: improvement or step back? (part 3)
- Get link
- X
- Other Apps
Windows 8.1: improvement or step back? (part 2)
- Get link
- X
- Other Apps
Windows 8.1: improvement or step back? (part 1)
- Get link
- X
- Other Apps
MacOsX Mavericks: free upgrade, no revolution (part 3)
- Get link
- X
- Other Apps
MacOsX Mavericks: free upgrade, no revolution (part 2)
- Get link
- X
- Other Apps
MacOsX Mavericks: free upgrade, no revolution ( part 1)
- Get link
- X
- Other Apps