Tips for an Information Security Analyst/Pentester career - Episode 10: Metasploitable 2
Intro
Metasploitable 2 is a deliberately vulnerable Linux distro, designed to safely practice hacking.
Metasploitable 2 is a deliberately vulnerable Linux distro, designed to safely practice hacking.
I've briefly dealt with Metasploitable 2 in my previous post Tips for an Information Security Analyst/Pentester career - Episode 2: Nmap and active recon (part 1).
Back there we used Metasploitable 2 as a legit target for our Nmap scans.
I had promised you I'd show you how to hack this VM, given its multiple vulnerabilities, and that's what we're gonna do.
Over this episode, I'm going to briefly show how to perform a successful attack, but a complete exploitation guide is available here.
Prep stage - recon
We start out with a typical Nmap stealth scan (-sS).
We find a lot of open ports and running services, as expected.
By running a Nessus scan, we can find four critical vulnerabilities.
By running a system versioning scan (-sV), we're able to have yet more intelligence on the services running on this vulnerable machine.
Exploitation stage
We notice a vulnerable Samba version is installed. Samba has been successfully exploited in one of the latest ransomware outbreaks, so we'll try leveraging this vulnerability to exploit the system.
Through Metasploit search functionality, we find several exploits available for the specific installed Samba version
I pick a Netbios exploit, running on port 139, so we launch the below command to use it.
In the exploit options, we setup RHOST as the IP address of the Metasploitable 2 VM (which I had previously setup with a NAT configuration), then we launch the exploit.
We can get a shell, so we're good to go.
It's not an interactive one, though it allows us to run commands.
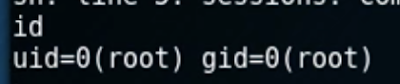
Checking the user id, we can confirm we're root.
As a simple demonstration that we're now within the vulnerable VM, I created a file called hacked! on the victim machine through the touch command.
Wrap-up
Metasploitable 2 is a very vulnerable VM used to safely practice hacking.
It's freely available for you to play with it.
The only caveat to it is you need to setup this VM with a host-only or custom network configuration, so that it's not accessible from the Internet.
This prevents your production system from being compromised through its exploitation.
Episode 11
Episode 9
Episode 11
Episode 9







Comments
Post a Comment