Search
TOOLS DON'T MAKE HACKERS, HACKERS MAKE TOOLS. An info sec junkie's professional path. Professional pentester and Red Teamer since October 2018. I love hacking and coding and I hope I can give my little knowledge back to the community and help make information systems more secure. This blog focuses on information security and white hat hacking, i.e. hacking based on the client's authorization. Hacking must be done responsibly: don't ruin people's lives and businesses.
Posts
Showing posts from December, 2016
Contact Form
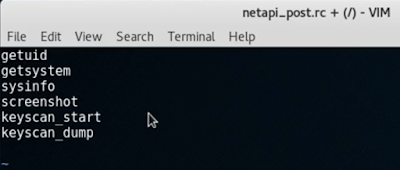
How to automate post exploitation with a Meterpreter script
- Get link
- Other Apps
How to create basic Snort IDS rules
- Get link
- Other Apps